For more samples, including user guides, troubleshooting guides, release notes, and white papers, send an email to marek.glinski0630@gmail.com.
Contents
- Part of a video delivery platform API
- Guide for creating webhooks
- Recipe for a Google Cloud Function
- API guide for a threat-hunting tool
- Knowledge base article for addressing a zero-day vulnerability
- Knowledge base article for troubleshooting a network issue in private clouds
- Guide for understanding vulnerability scan reports
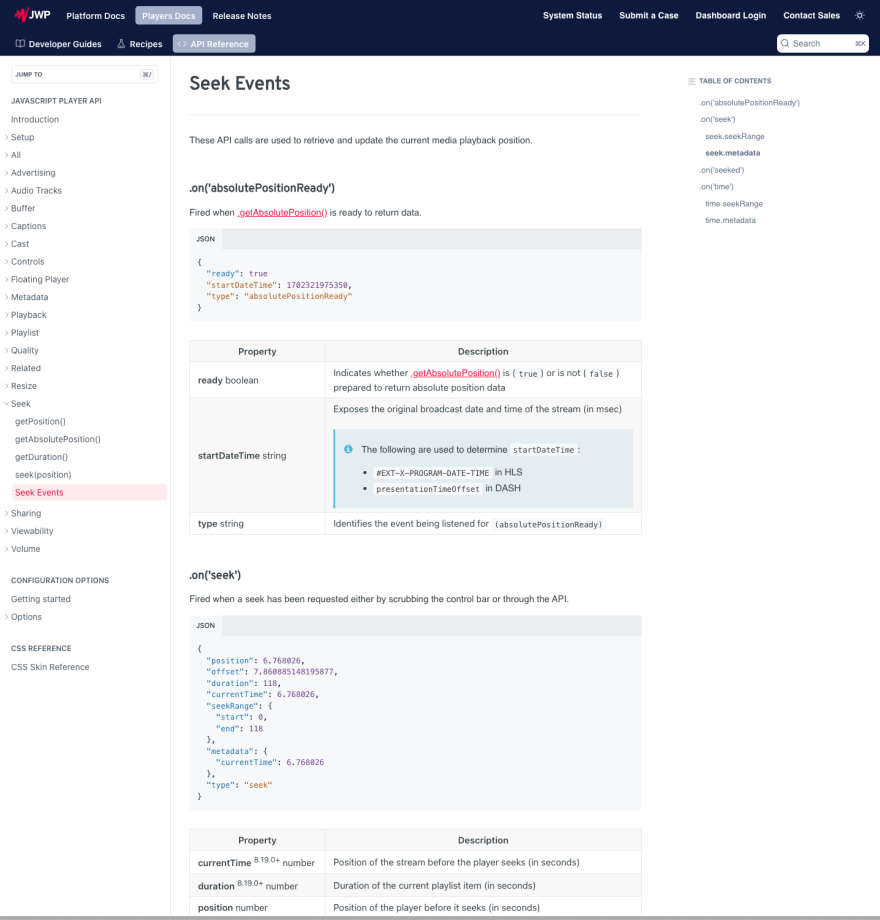
Part of a video delivery platform API
JWPlayer, video platform provider
Problem/Solution: Developers using this video player API need to understand events that are triggered when the player’s playback position changes. This page helps them learn about the properties within JSON objects returned during these playback events.
This screen shot shows part of the page. See the full live page.
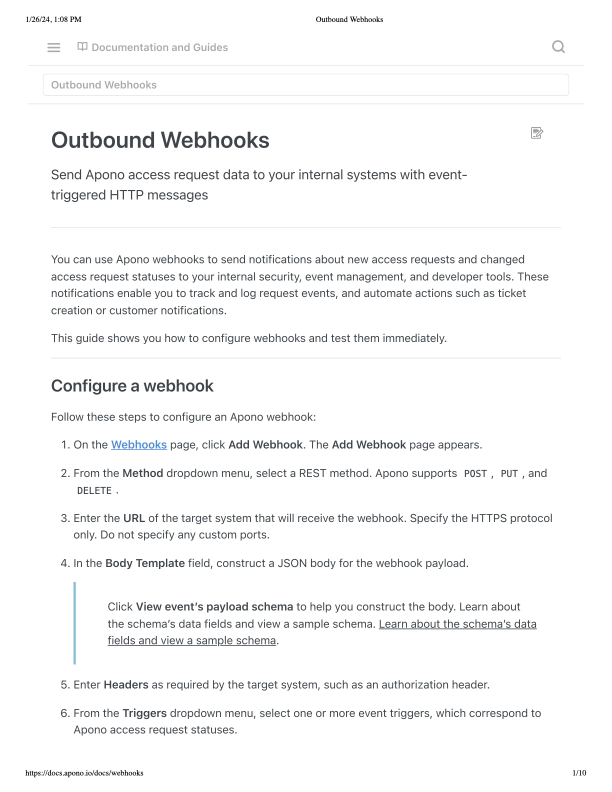
Guide for creating webhooks
Apono, a cloud access management provider
Problem/solution: Developers need to automate delivery of access request notification events to administrators of cloud resources. This guide provides step-by-step guidance for creating and testing webhooks in a platform UI. Additionally, it provides a reference for creating webhook JSON payloads based on a complex schema.
This screenshot shows the first page of the guide. See the live page for the complete guide.
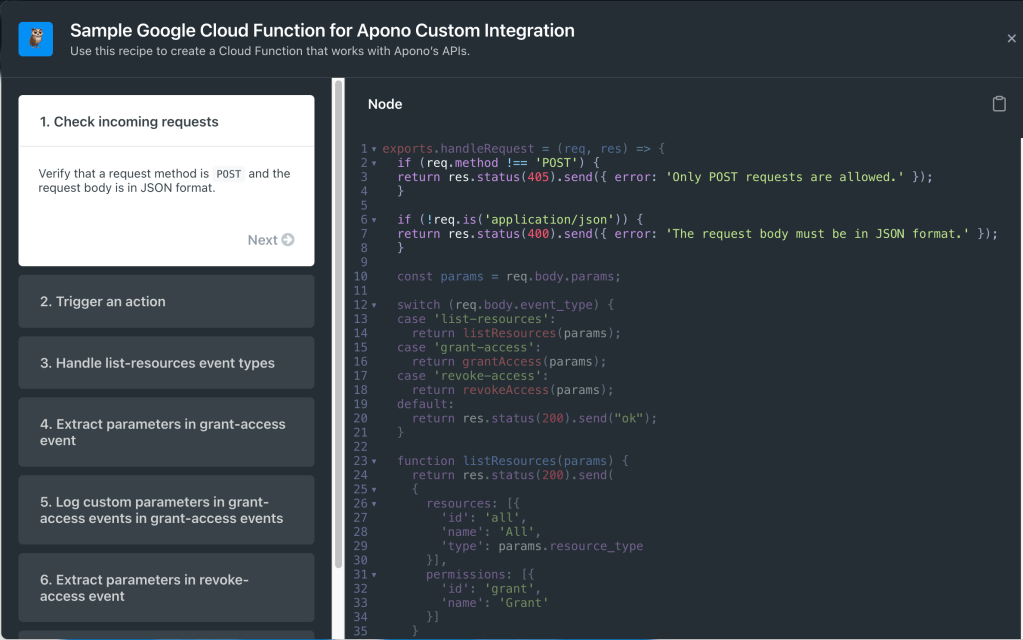
Recipe for a Google Cloud Function
Apono, a cloud access management provider
Problem/solution: Developers need to connect their internal applications to Google Cloud Functions and manage access to those applications with Apono. This recipe gives them step-by-step guidance to create relevant functions.
This screenshot shows one step of the recipe. See the live page for the complete recipe.
API guide for a threat-hunting tool
SecurityScorecard, security ratings company
Problem/solution: Threat hunters need to understand how to access and make sense of the massive amount of data that Attack Surface Intelligence tool provides. This guide helps them use the API to correlate information about publicly exposed digital assets, their cybersecurity vulnerabilities, and threat actors known to exploit these vulnerabilities.
This screen shot shows three pages. Download the PDF of the full guide.
Note: Hyperlinks are disabled in the PDF. I included them to help show the structure of the guide.
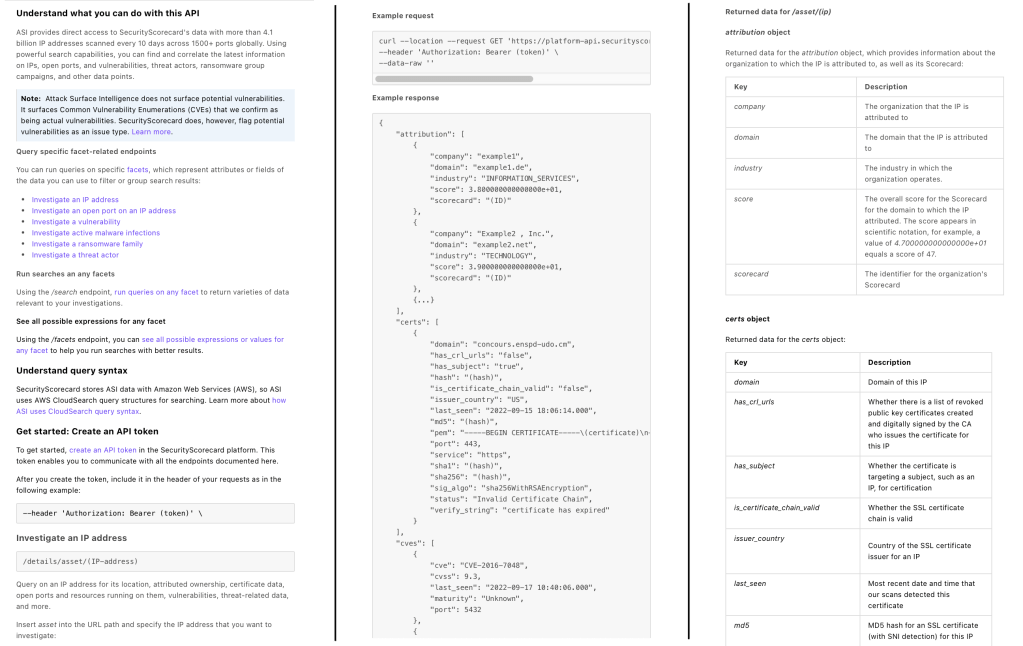
Knowledge base article for addressing a zero-day vulnerability
SecurityScorecard, security ratings company
Problem/solution: Security professionals need to respond quickly to a critical zero-day vulnerability, especially given some high-profile attacks that had occurred since its discovery. This article helps customers understand the business risk and take clear steps to investigate and remediate the vulnerability in their security ecosystems.
This screen shot shows four pages. Download the PDF of the full article.
Note: Hyperlinks are disabled in the PDF. I included them to help show the structure of the guide.
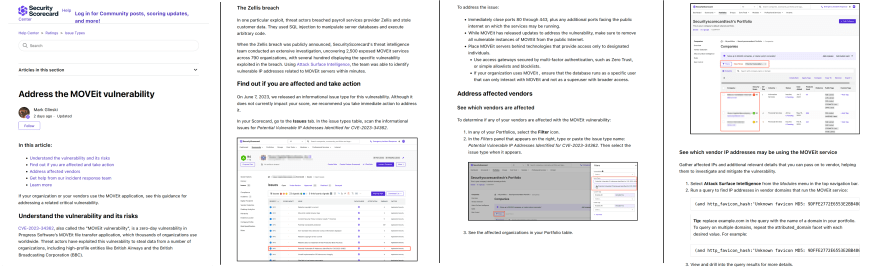
Knowledge base article for troubleshooting a network issue in private clouds
Metacloud, private cloud platform provider acquired by Cisco Systems
Problem/solution: When trying to build and deploy private clouds, customers struggle with management of DHCP ports and often ran into problems. This article addresses one of the most frequently reported Support issues by helping customers restore deleted DHCP ports. It also provides best practices for managing these ports.
This screen shot shows two pages. Download the PDF of the full article.
Note: Hyperlinks are disabled in the PDF. I included them to help show the structure of the guide.
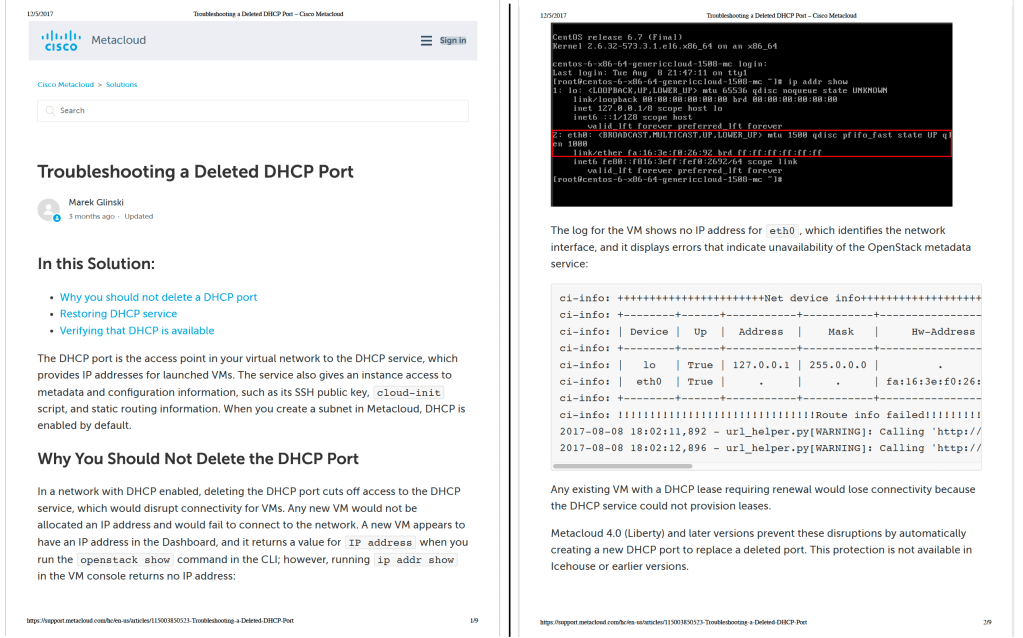
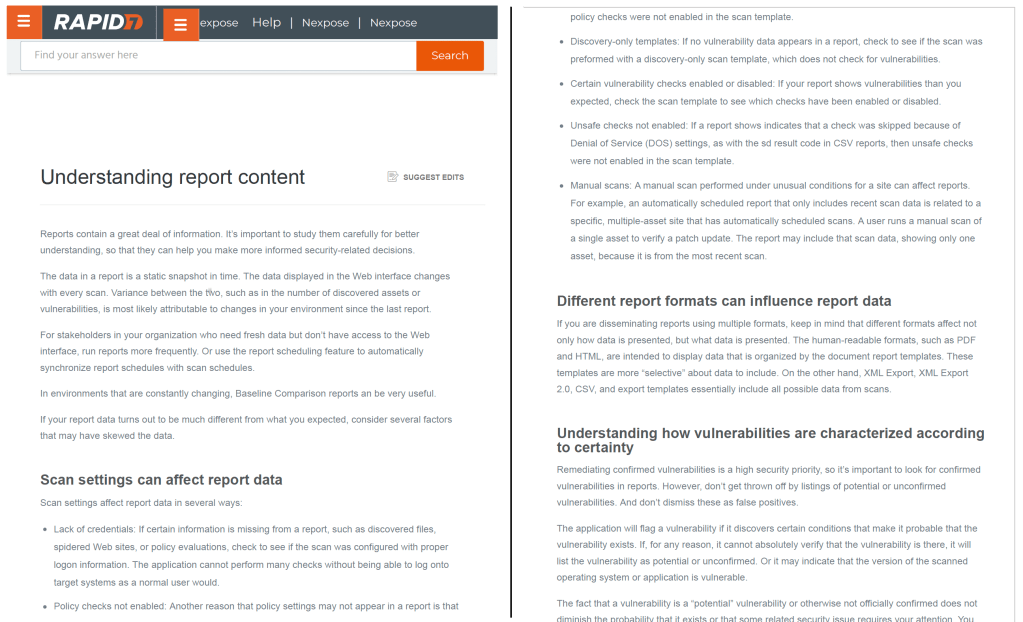
Guide for understanding vulnerability scan reports
Organization: Rapid7, public cybersecurity company
Problem/Solution: Customers struggle to make sense of the massive amount of information in vulnerability scan reports. This guide answers common questions and provided clear business context for the report data, so that customers could gain better insights and take necessary actions.
This screen shot shows two pages. Download the PDF of the full guide.
Note: Hyperlinks are disabled in the PDF. I included them to help show the structure of the guide.